Multi-factor authentication (MFA)
Multi-factor authentication (MFA), also known as two-factor authentication (2FA), is a security mechanism that requires users to provide two or more forms of authentication before granting access to a system or application. MFA adds an additional layer of security beyond traditional username-and-password combinations, significantly enhancing the protection of sensitive data and accounts.
It is important to implement MFA for database access, which means that users need to provide an additional form of authentication, such as a code from a mobile app, along with their password. This prevents unauthorized access even if passwords are compromised.
The following figure depicts the basic setup of MFA on the AWS cloud:
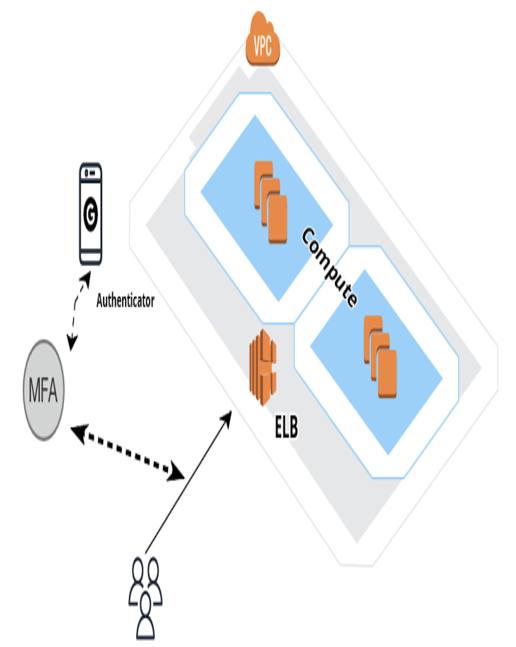
Figure 9.2: MFA setup on the AWS cloud
The preceding diagram shows how users are able to access the cloud system using the MFA service that is closely coupled with the authenticator, which could be a device such as a user’s phone.
Key aspects of MFA are as follows:
- Enhanced security: MFA reduces the risk of unauthorized access by requiring multiple forms of verification
- Mitigation of credential theft: Even if passwords are compromised, the additional authentication factors provide an extra barrier against unauthorized access
- Adaptive authentication: Some MFA systems use adaptive techniques to adjust authentication requirements based on user behavior and risk profiles
Authentication factors are as follows:
- Something you know: This is typically a password or PIN
- Something you have: This includes a physical device such as a smartphone, security token, or smart card
- Something you are: This refers to biometric factors such as fingerprints, facial recognition, or voice recognition
Implementing MFA involves the following:
- Selecting MFA methods: Choose appropriate authentication factors based on the level of security required and user convenience
- User enrollment: Guide users through the process of enrolling their chosen authentication methods
- Authentication process: When accessing a system, users are prompted to provide multiple forms of authentication
Tools and methods for MFA include the following:
- Authentication apps:
• Google Authenticator: Generates time-based one-time passwords (TOTP)
• Microsoft Authenticator: Provides TOTP and push-based authentication - Hardware tokens:
• YubiKey: Hardware security token that supports multiple authentication methods
• RSA SecurID: Provides hardware tokens for MFA - Biometric authentication:
• Apple Face ID and Touch ID: Use facial recognition and fingerprint scanning for authentication
• Windows Hello: Provides biometric authentication for Windows devices - SMS and email codes:
• Authentication codes are sent via SMS or email for users to enter during login - Adaptive MFA:
• Azure Active Directory Conditional Access: Adjusts MFA requirements based on user behavior - Cloud identity providers:
• AWS IAM: Supports MFA for securing AWS accounts
• Google Cloud Identity Platform: Provides MFA for Google Cloud services
MFA is a powerful tool for preventing unauthorized access, especially in cloud environments where remote access is common. By requiring multiple forms of authentication, MFA significantly reduces the risk of data breaches resulting from compromised passwords or credentials.
By adhering to these database security best practices and customizing them to the specific requirements of the organization, businesses can mitigate risks, comply with regulations, and build a secure foundation for their cloud-based data storage and management.
The following Database high-availability and scalability features section delves into the critical considerations and techniques for ensuring that databases hosted in the cloud are highly available and capable of scaling to meet evolving demands. In today’s data-driven landscape, databases form the backbone of applications, making their availability and scalability paramount. This section explores concepts such as database replication, clustering, sharding, and autoscaling, which empower organizations to maintain continuous access to their data and adapt to changing workloads without compromising performance. By understanding these strategies and leveraging cloud-native tools, readers will be equipped to design and manage robust and responsive database systems that align with modern application requirements.